Researchers from IBM Research Europe and VU Amsterdam detail a new cross-platform speculative execution attack in modern CPUs to access passwords and other sensitive data. Their GhostRace paper was published at the 33rd USENIX Security Symposium 2024.
On March 12, researchers from VUSec and IBM published a new form of speculative execution attack in X, citing the corresponding GhostRace disclosure document posted on VUSec. But first, let’s take a moment to define what a “speculative execution attack” is.
If you remember the Meltdown and Spectre disasters in 2016, this vulnerability is almost in the same category of CPU security exploits and is very similar to Spectre V1, as it is also a speculative execution attack.
Speculative execution is an optimization method where the processor calculates some tasks in advance, the result of which may or may not be needed later (which will speed up execution).
The problem is that speculative execution can also lead to “races” where individual threads trying to access shared resources create serious security vulnerabilities by exploiting flaws in the execution sequence itself. This exploit is aimed at exploiting such scenarios, which is why it is appropriately named GhostRace.
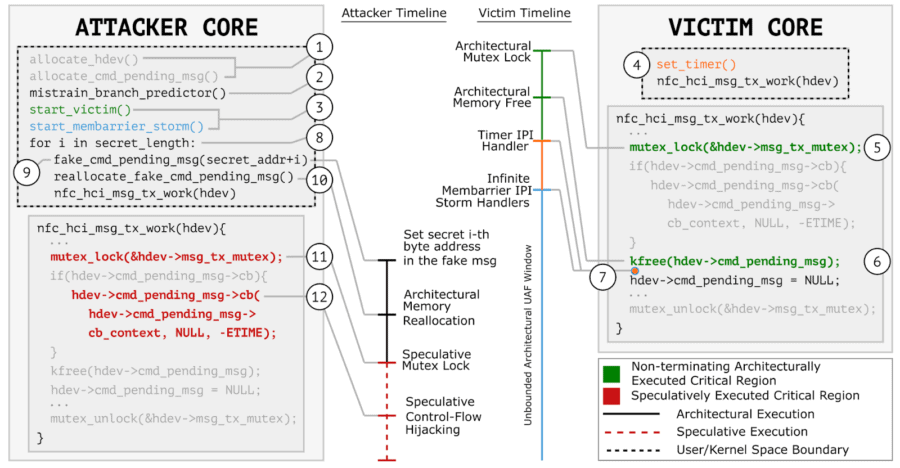
Before making GhostRace public, the researchers notified the major hardware vendors (Intel, AMD, ARM, and IBM) and the Linux kernel of the problem (in late 2023), as GhostRace applies to all major CPU architectures (not just x86, but also ARM).
Hardware vendors have additionally notified other affected software vendors (OS/hypervisors), and all parties have acknowledged the reported issue (CVE-2024-2193).
Being made public only on March 12, 2024, gave vendors the time they needed to develop their patches and workarounds, but the researchers also included some tips on how to mitigate the problem in the public document.
An early attempt to patch the Linux kernel seemed promising, but experiments conducted by the researchers showed that the patch did not fully cover the vulnerability.
At this point, it seems that the Linux kernel developers are primarily concerned about performance and don’t want to risk seriously damaging it with a quick fix. The off-the-shelf mitigation for Linux provided in the original documentation only reduces performance by ~5% in LMBench.
We expect that further fixes may improve performance. The document does not provide fixes for other platforms. However, AMD recognizes the problem and emphasizes that the existing Spectre v1 patches reduce the vulnerability from GhostRace.

Loading comments …